We’re all no strangers to scams and phishing attempts. We receive them on a daily basis in texts, emails, phone calls, and even traditional mail. Some are easier to spot than others. It’s become necessary to take a hard look at any and all incoming messages in order to protect your privacy and personal information.
The recruiting and staffing space is no stranger to scams, phishing, and brand impersonations, amongst other cyber crimes. Many of our counterparts in the industry have faced these challenges – and now it’s hit home.
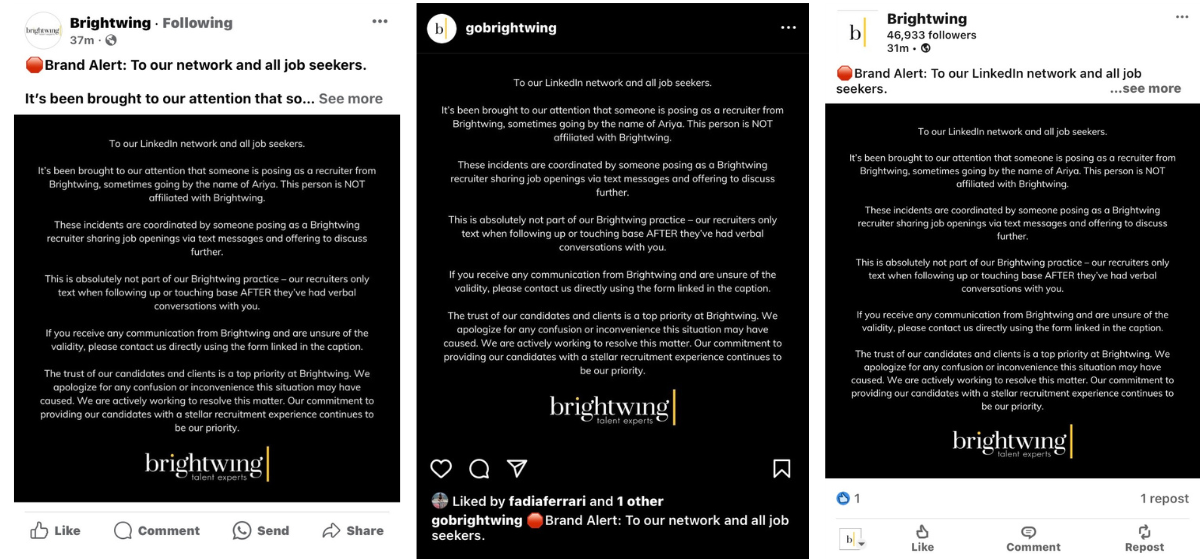
We’ve recently received multiple reports at Brightwing of brand impersonation and phishing attempts. Here’s how we’re handling them.
Respond to reports
Someone posing as a Brightwing recruiter, using the same name each time, was reaching out to people through text messages offering open job opportunities. A handful of well-wishers had the foresight to reach out to us after feeling skeptical about the messages they received. The reports were consistent every time. We ruled out a security breach since none of the incidents involved candidates in our database.
Through a stream of reports, we realized that someone was impersonating the Brightwing brand.
Traceback their trail
If these incidents are taking place through email messages, we recommend doing some detective work. You may be able to identify the email server they’re using and report them to the server; this will flag and shut down the account.
While it’s more challenging to trace back through text message attempts, there are ways you can do to get in touch with the impersonator. If you have access to the phishing attempts, respond to the impersonator and play along with them. See how far they go, and how much information they can reveal in order for you to report them. Dare to even confront them.
Lastly, remember to report these as cyber crimes on credible sites like the Internet Crime Complaint Center (IC3)
Keep an active log
We’re keeping an active log of all attempts in a spreadsheet with names of individuals who reported incidents, contact information, and a copy of the messages received. The more information you collect, the better you can respond to concerned stakeholders and develop a response plan to this issue.
Communicate what is happening with internal stakeholders
Collect information on the incidents and let your leadership team know what is happening. Some things we looked into at Brightwing when sharing these incidents with leadership are the state where the reports have occurred, the phone number, the name of the fake recruiter, whether or not any candidates in our database were affected, etc. The goal is to look for patterns that help you narrow where to look and how to respond.
Visibility across your greater team is important as well. We notified our recruiters and business development team so they’re aware of what’s happening and how we are responding. It’s also good practice for recruiters to set expectations with their candidates on what channels they plan to use for communication.
Communicate with external stakeholders
Communicate to your professional network on what is happening. Transparency with our network is important, so we released a statement on our LinkedIn page and our Contact Us page warning about the phishing and brand impersonation attempts happening in Brightwing’s name. We communicated that we are diligently working on this and that this doesn’t harm existing candidates or clients.
Looking Ahead
It’s an uneasy feeling to know someone is out there using the name you’ve spent decades building. This is an active and evolving process. We’re actively responding to this and looking for ways to prevent future attempts.
let’s talk
SEND US A MESSAGE

